Trezor Login – Secure | Access to Your Crypto
When it comes to protecting your digital assets, Trezor offers one of the most secure and user-friendly solutions in the crypto world. The Trezor login process is uniquely designed to ensure maximum security without relying on traditional usernames or passwords. Instead, access is granted through your Trezor hardware wallet, making your private keys and funds virtually immune to online threats.
What Is Trezor?
Trezor is a hardware wallet developed by SatoshiLabs that lets you store, manage, and protect your cryptocurrencies offline. With models like the Trezor Model One and Trezor Model T, it offers unparalleled security by keeping your private keys offline, away from hackers, phishing attempts, or malware.
How Trezor Login Works
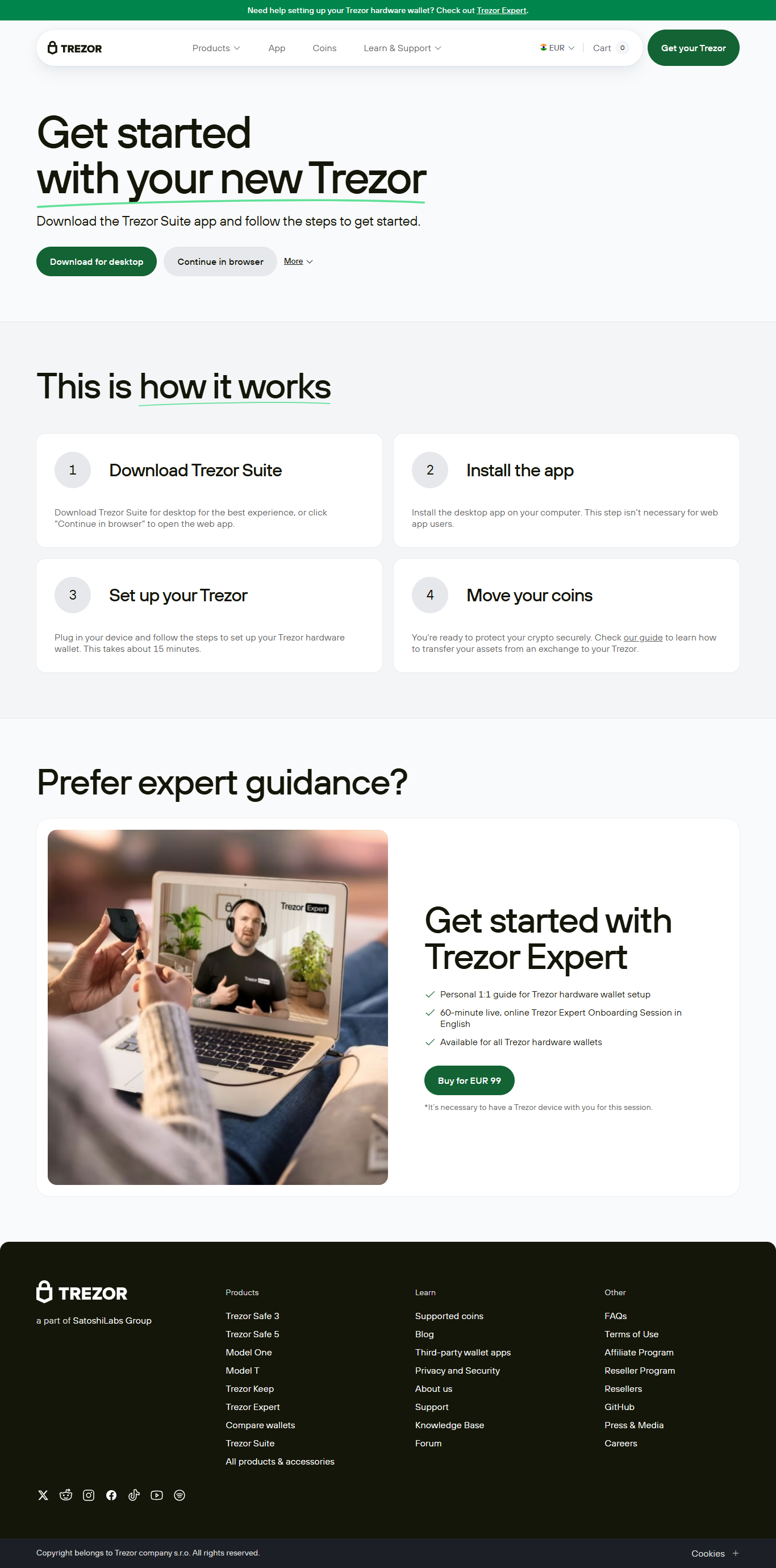
Logging into your Trezor wallet is different from standard platforms. Here’s how you securely access your account using Trezor Suite:
- Connect Your Trezor Device Plug your Trezor into your computer or smartphone using a USB cable.
- Open Trezor Suite Launch the Trezor Suite desktop app or access the web version.
- Run Trezor Bridge If you’re using the web version, ensure Trezor Bridge is installed for communication between your device and browser. You can download it from trezor.io/bridge.
- Enter PIN on Device Your PIN is entered directly on your Trezor device, protecting it from keyloggers.
- Optional: Enter Passphrase If you’ve enabled a passphrase, you’ll be prompted to input it either on your computer or device.
- Access Your Wallet Dashboard Once authenticated, you’ll enter your Trezor Suite dashboard to manage your portfolio securely.
Why Trezor Login Is More Secure
- No passwords to steal – your hardware wallet is your key.
- Private keys never leave the device – no exposure to online threats.
- Encrypted communication between your device and Trezor Suite.
- 2-Factor authentication built-in via the physical device.
With Trezor login, even if your computer is compromised, your crypto stays safe.
Benefits of Using Trezor
- Supports hundreds of coins including Bitcoin, Ethereum, Litecoin, and ERC-20 tokens.
- Built-in integration with platforms like Exodus, MetaMask, and WalletConnect.
- Offline storage (cold wallet) means ultimate protection from hackers.
- Easy-to-use interface via Trezor Suite with real-time balance tracking and portfolio insights.
Made in Typedream